Five Eyes (FVEY)
Posted: Tue Nov 02, 2021 12:53 pm
The revelations of 2013 – made possible by NSA-whistleblower Edward Snowden – on the reach and scope of global surveillance practices have prompted a fundamental re-examination of the role of intelligence services in conducting coordinated cross-border surveillance. The Five Eyes alliance – comprised of the United States National Security Agency (NSA), the United Kingdom’s Government Communications Headquarters (GCHQ), Canada’s Communications Security Establishment Canada (CSEC), the Australian Signals Directorate (ASD), and New Zealand’s Government Communications Security Bureau (GCSB) – is the continuation of an intelligence partnership formed in the aftermath of the Second World War. The patchwork of secret spying programmes and intelligence-sharing agreements implemented by parties to the Five Eyes arrangement constitutes an integrated global surveillance arrangement that now covers the majority of the world’s communications. Operating in the shadows and misleading the public, the Five Eyes agencies boast in secret how they “have adapted in innovative and creative ways that have led some to describe the current day as ‘the golden age of SIGINT [signals intelligence]
The Five Eyes (FVEY) is an intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States. These countries are parties to the multilateral UKUSA Agreement, a treaty for joint cooperation in signals intelligence
Secret agreements allow secretive intelligence agencies in Australia, Canada, New Zealand, the United Kingdom, and the USA to spy on the world.
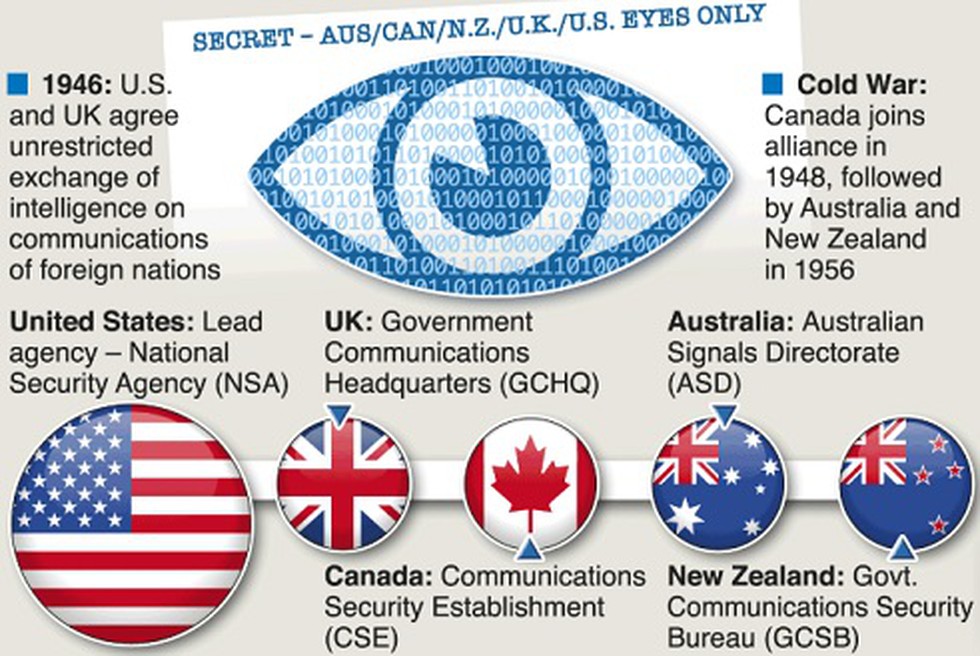
Beginning in 1946, an alliance of five countries (the US, the UK, Australia, Canada and New Zealand) developed a series of bilateral agreements over more than a decade that became known as the UKUSA (pronounced yew-kew-zah) agreement. This established the “Five Eyes” alliance for the purpose of sharing intelligence, but primarily signals intelligence (hereafter “SIGINT”). The close relationship between the five states is evidenced by documents recently released by Snowden. Almost all of the documents include the classification “TOP SECRET//COMINT//REL TO USA, AUS, CAN, GBR, NZL” or “TOP SECRET//COMINT//REL TO USA, FVEY”. These classification markings indicate the material is top-secret communications intelligence (aka SIGINT) material that can be released to the US, Australia, Canada, UK and New Zealand. Notably while other alliances and coalitions exist, such as the North Atlantic Treaty Organization, none of the documents that have thus far been made public refer to any of these arrangements, suggesting the Five Eyes alliance is the preeminent SIGINT collection alliance.
The Five Eyes agencies are playing a dirty game. They have found ways to infiltrate all aspects of modern communications networks: forcing companies to hand over their customers’ data under secret orders, and secretly tapping fibre optic cables between the same companies’ data centres anyway; accessing sensitive financial data through SWIFT, the world’s financial messaging system; spending years negotiating an international agreement to regulate access to the data through a democratic and accountable process, and then hacking the networks to get direct access; threatening politicians with trumped-up threats of impending cyber war while conducting intrusion operations that weaken the security of networks globally; and sabotaging encryption standards and standards bodies, thereby undermining the ability of internet users to secure information.
The Five Eyes is a close-knit group. The level of cooperation under the UKUSA agreement is so complete that "the national product is often indistinguishable."3 This has resulted in former intelligence officials explaining that the close-knit cooperation that exists under the UKUSA agreement means “that SIGINT customers in both capitals seldom know which country generated either the access or the product itself.”4 In addition to fluidly sharing collected SIGINT, it is understood that many intelligence facilities run by the respective Five Eyes countries are jointly operated, even jointly staffed, by members of the intelligence agencies of Five Eyes countries. Each facility collects SIGINT, which can then be shared with the other Five Eyes states.
Code-named programmes that have been revealed to the public over the last decade go some way to illustrating how the Five Eyes alliance collaborates on specific programmes of activity and how information is shared. One important example is the TEMPORA programme, revealed by Snowden. By placing taps at key undersea fibre-optic cable landing stations, the programme is able to intercept a significant portion of the communications that traverse the UK. The Guardian has reported that 300 analysts from GCHQ and 250 from the NSA were directly assigned to examine material collected. 5 TEMPORA stores content for three days and metadata for 30 days.
Once content and data are collected, they can be filtered. The precise nature of GCHQ’s filters remains secret. Filters could be applied based on type of traffic (e.g. Skype, Facebook, email), origin/destination of traffic, or to conduct basic keyword searches, among many other purposes. Reportedly, approximately 40,000 search terms have been chosen and applied by GCHQ, and another 31,000 by the NSA to information collected via TEMPORA. GCHQ have had staff examining collected material since the project’s inception in 2008, with NSA analysts brought to trial runs of the technology in summer 2011. Full access was provided to NSA by autumn 2011. An additional 850,000 NSA employees and US private contractors with top-secret clearance reportedly also have access to GCHQ databases. GCHQ received £100 million (USD 160 million) in secret NSA funding over the last three years to assist in the running of this project. 6
A core programme that provides filtering capability is known as XKEYSCORE. It has been described by internal NSA presentations as an “analytic framework” which enables a single search to query a “3-day rolling buffer” of “all unfiltered data” stored at 150 global sites on 700 database servers.7 The NSA XKEYSCORE system has sites that appear in Five Eyes countries. 8 The system indexes email addresses, file names, IP addresses and port numbers, cookies, webmail and chat usernames and buddylists, phone numbers, and metadata from web browsing sessions including searches queried, among many other types of data that flow through their collection points.
While UKUSA is often reported as having created a “no spy pact” between Five Eyes states, there is little in the original declassified documents from the 1940s and 1950s to support such a notion. Crucially, first and foremost, no clause exists that attempts in any form to create such an obligation. As best as can be ascertained, it seems there is no prohibition on intelligence gathering by Five Eyes states with respect to the citizens or residents of other Five Eyes states. There is instead, it seems, a general understanding that citizens will not be directly targeted, and where communications are incidentally intercepted, there will be an effort to minimise the use and analysis thereof by the intercepting state. Outside the Five Eyes, everyone else is fair game, even if they have a separate intelligence-sharing agreement with one or several Five Eyes members.
The rights implications
The world has changed dramatically since the 1940s; then, private documents were stored in filing cabinets under lock and key, and months could pass without one having the need or luxury of making an international phone call. Now, private documents are stored in unknown data centres around the world, international communications are conducted daily, and our lives are lived – ideas exchanged, financial transactions conducted, intimate moments shared – online.
With the advent of the internet and new digital forms of communication, now most digital communications take the fastest and cheapest route to their destination, rather than the most direct. This infrastructure means that the sender has no ability to choose, nor immediate knowledge of, the route that their communication will take. This shift in communications infrastructure means that communications travel through many more countries, are stored in a variety of countries (particularly through the growing popularity of cloud computing) and are thus vulnerable to interception by multiple intelligence agencies. From their bases within the territory of each country, each Five Eyes intelligence agency collects and analyses communications that traverse their territory and beyond.
An analysis of the legal provisions in each of the Five Eyes countries reveals that they fall far short of describing the fluid and integrated intelligence-sharing activities that take place under the ambit of the Five Eyes arrangement with sufficient clarity and detail to ensure that individuals can foresee their application. 10 None of the domestic legal regimes set out the circumstances in which intelligence authorities can obtain, store and transfer nationals’ or residents’ private communication and other information that are intercepted by another Five Eyes agency, nor which will govern the circumstances in which any of the Five Eyes states can request the interception of communications by another party to the alliance. The same applies to obtaining private information such as emails, web histories, etc., held by internet and other telecommunication companies. Carefully constructed legal frameworks provide differing levels of protections for internal versus external communications, or those relating to nationals versus non-nationals.
The Five Eyes agencies are seeking not only to defeat the spirit and purpose of international human rights instruments, they are in direct violation of their obligations under such instruments. The right to privacy is an internationally recognised right.11 The way the global communications infrastructure is built requires that the right to privacy of communications can be exercised globally, as communications can be monitored in a place far from the location of the individual to whom they belong. When an individual sends a letter, email or text message, or makes a phone call, that communication leaves their physical proximity, and travels to its destination. In the course of its transmission the communication may pass through multiple other states and, therefore, multiple jurisdictions. The right to privacy of the communication remains intact, subject only to the permissible limitations set out under human rights law. Accordingly, whenever Five Eyes countries interfere with the communication of an individual, thus infringing upon their privacy, they invoke jurisdiction over that individual, and have to comply with human rights obligations accordingly.
The practice of mass surveillance detailed in the Snowden documents is contrary to international law. The Special Rapporteur on the promotion and protection of the right to freedom of expression and opinion, for example, has described the invasiveness of mass interception of fibre-optic cables: “By placing taps on the fibre optic cables, through which the majority of digital communication information flows, and applying word, voice and speech recognition, States can achieve almost complete control of tele- and online communications.”12
The Special Rapporteur reasons that “[m]ass interception technology eradicates any considerations of proportionality, enabling indiscriminate surveillance. It enables the State to copy and monitor every single act of communication in a particular country or area, without gaining authorization for each individual case of interception.
Taking action
The intelligence agencies of the Five Eyes countries conduct some of the most important, complex and far-reaching activities of any state agency, and they do so behind the justification of a thicket of convoluted and obfuscated legal and regulatory frameworks. The laws and agreements that make up the Five Eyes arrangement and apply it to domestic contexts lack any semblance of the clarity or accessibility necessary to ensure that the individuals whose rights and interests are affected by them are able to understand their application. Their actions have been justified in secret, on the basis of secret interpretations of international law and classified agreements. By remaining in the shadows, our intelligence agencies – and the governments who control them – have removed our ability to challenge their actions and their impact upon our human rights. We cannot hold our governments accountable when their actions are obfuscated through secret deals and covert legal frameworks. Secret, convoluted or obfuscated law can never be considered law within a democratic society governed by the rule of law.
We must move towards an understanding of global surveillance practices as fundamentally opposed to the rule of law and to the well-established international human right to privacy. In doing so, we must break down legal frameworks that obscure the activities of the intelligence agencies or that preference the citizens or residents of Five Eyes countries over the global internet population. Trust must be restored, and our intelligence agencies must be brought under the rule of law. Transparency around and accountability for secret agreements is a crucial first step.
Privacy International has spent the last year trying to unpick the Five Eyes alliance. We have sent freedom of information requests to intelligence agencies in each of the five countries, seeking access to the secret agreements that govern the Five Eyes. We have brought legal cases against Britain’s GCHQ for mass surveillance and hacking activities, and have sought avenues to take similar complaints in other jurisdictions. We filed a complaint under the OECD Guidelines for Multinational Enterprises against the seven telecommunications companies facilitating UK interception of fibre-optic cables. We have written to the Australian Inspector-General of Intelligence and Security asking her to commence an investigation into the ASD, and to the US Treasury Department and to every data protection authority in Europe seeking an investigation into the SWIFT hacking.
-
The origins of the FVEY can be traced to informal secret meetings during World War II between British and American code-breakers, which started before the U.S. formally entered the war, followed by the Allies'1941 Atlantic Charter that established their vision of the post-war world. Canadian academic Srdjan Vucetic argues the alliance emerged from Winston Churchill's Iron Curtain speech in 1946, which warned of open conflict with the Soviet bloc unless the English-speaking democracies learned to cooperate:
Neither the sure prevention of war, nor the continuous rise of world organisation will be gained without what I have called the fraternal association of the English-speaking peoples. This means a special relationship between the British Commonwealth and Empire and the United States... the continuance of the intimate relationship between our military advisers, leading to common study of potential dangers..."
As the Cold War deepened, the intelligence sharing arrangement became formalised under the ECHELON surveillance system in the 1960s. This was initially developed by the FVEY to monitor the communications of the former Soviet Union and the Eastern Bloc, although it is now used to monitor communications worldwide.
In the late 1990s, the existence of ECHELON was disclosed to the public, triggering a major debate in the European Parliament and, to a lesser extent, the United States Congress. The FVEY further expanded their surveillance capabilities during the course of the "war on terror", with much emphasis placed on monitoring the World Wide Web. Former NSA contractor Edward Snowden described the Five Eyes as a "supra-national intelligence organisation that does not answer to the known laws of its own countries". Documents leaked by Snowden in 2013 revealed that the FVEY has been spying on one another's citizens and sharing the collected information with each other in order to circumvent restrictive domestic regulations on surveillance of citizens.
In spite of continued controversy over its methods, the Five Eyes relationship remains one of the most comprehensive known espionage alliances in history.
Since processed intelligence is gathered from multiple sources, the intelligence shared is not restricted to signals intelligence (SIGINT) and often involves defence intelligence as well as human intelligence (HUMINT) and geospatial intelligence (GEOINT).
Origins (1941–1950s)
The earliest origins of the Five Eyes alliance are secret meetings between British and US code-breakers at the British code-breaking establishment at Bletchley Park in February 1941 (before the US entry into the war). A February 1941 entry in the diary of Alastair Denniston, head of Bletchley Park, reading "The Ys are coming!" ("Ys" referring to "Yanks") is the first record, followed by "Ys arrive" on 10 February. The British and US agencies shared extremely confidential information, including the British breaking of the German Enigma code, and the US breaking of the Japanese Purple code. From then key figures travelled back and forth across the Atlantic, including Denniston and code-breaking expert Alan Turing. The practical relationship established for wartime signals intelligence developed into a formal signed agreement at the start of the post-war Cold War.[16]
The formal Five Eyes alliance can be traced back to the Atlantic Charter, which was issued in August 1941 to lay out the Allied goals for the post-war world. On 17 May 1943, the British–U.S. Communication Intelligence Agreement, also known as the BRUSA Agreement, was signed by the UK and U.S. governments to facilitate co-operation between the U.S. War Department and the British Government Code and Cypher School (GC&CS). On 5 March 1946, the secret treaty was formalized as the UKUSA Agreement, which forms the basis for all signal intelligence cooperation between the NSA and GCHQ to this day.
In 1948, the treaty was extended to include Canada, followed by Norway (1952), Denmark (1954), West Germany (1955), Australia (1956), and New Zealand (1956). These countries participated in the alliance as "third parties". By 1955, the formal status of the remaining Five Eyes countries was officially acknowledged in a newer version of the UKUSA Agreement that contained the following statement:
At this time only Canada, Australia and New Zealand will be regarded as UKUSA-collaborating Commonwealth countries.
The "Five Eyes" term has its origins as a shorthand for a "AUS/CAN/NZ/UK/US EYES ONLY" (AUSCANNZUKUS) releasability caveat.
Cold War
During the Cold War (generally accepted to be approximately the period 1947-1991), GCHQ and the NSA shared intelligence on the Soviet Union, the People's Republic of China, and several eastern European countries (known as Exotics).[20] Over the course of several decades, the ECHELON surveillance network was developed to monitor the military and diplomatic communications of the Soviet Union and its Eastern Bloc allies.
During the Vietnam War, Australian and New Zealand operators in the Asia-Pacific region worked directly to support the United States, while GCHQ operators stationed in the (then) British colony of Hong Kong were tasked with monitoring North Vietnamese air defence networks. During the Falklands War, the British received intelligence data from its FVEY allies such as Australia, as well as from third parties such as Norway and France. In the aftermath of the Gulf War, a technician of the ASIS was used by SIS to bug Kuwaiti government offices.
In the 1950s, SIS and the CIA jointly orchestrated the overthrow of Iran's Prime Minister Mohammad Mosaddegh. In the 1960s, SIS and the CIA jointly orchestrated the assassination of the Congolese independence leader Patrice Lumumba. In the 1970s, the ASIS and the CIA jointly orchestrated the overthrow of Chile's President Salvador Allende. During the Tiananmen Square protests of 1989, SIS and the CIA took part in Operation Yellowbird to rescue dissidents from the Chinese regime.
ECHELON network disclosures (1972–2000)
By the end of the 20th century, the ECHELON surveillance network had evolved into a global system capable of sweeping up massive amounts of private and commercial communications, including telephone calls, fax, e-mail and other data traffic. This was done through the interception of communication bearers such as satellite transmission and public switched telephone networks.
The Five Eyes has two types of information collection methods: the PRISM program and the Upstream collection system. The PRISM program gathers user information from technology firms such as Google, Apple and Microsoft, while the Upstream system gathers information directly from the communications of civilians via fiber cables and infrastructure as data flows past. The program's first disclosure to the public came in 1972 when a former NSA communications analyst reported to Ramparts Magazine that the NSA had developed technology that "could crack all Soviet codes". In 1988, Duncan Campbell revealed in the New Statesman the existence of ECHELON, an extension of the UKUSA Agreement on global signals intelligence [Sigint]. The story, 'Somebody's listening,' detailed how the eavesdropping operations were not only being employed in the interests of 'national security,' but were regularly abused for corporate espionage in the service of US business interests. The piece passed largely unnoticed outside of journalism circles. In 1996, a detailed description of ECHELON was provided by New Zealand journalist Nicky Hager in a book titled "Secret Power – New Zealand's Role in the International Spy Network", which was cited by the European Parliament in a 1998 report titled "An Appraisal of the Technology of Political Control" (PE 168.184). On 16 March 2000, the Parliament called for a resolution on the Five Eyes and their ECHELON surveillance network, which, if passed, would have called for the "complete dismantling of ECHELON".
Three months later, the Temporary Committee on ECHELON was set up by the European Parliament to investigate the ECHELON surveillance network. However, according to a number of European politicians such as Esko Seppänen of Finland, these investigations were hindered by the European Commission.
In the United States, congressional legislators warned that the ECHELON system could be used to monitor U.S. citizens. On 14 May 2001, the U.S. government cancelled all meetings with the Temporary Committee on ECHELON.
According to a BBC report in May 2001, "the US Government still refuses to admit that Echelon even exists.
War on Terror (since 2001)
In the aftermath of the September 11 attacks on the World Trade Center and the Pentagon, the surveillance capabilities of the Five Eyes were greatly increased as part of the global War on Terror.
During the run-up to the Iraq War, the communications of UN weapons inspector Hans Blix were monitored by the Five Eyes. The office of UN Secretary-General Kofi Annan was bugged by British agents. An NSA memo detailed plans of the Five Eyes to boost eavesdropping on UN delegations of six countries as part of a "dirty tricks" campaign to apply pressure on these six countries to vote in favour of using force against Iraq.
SIS and the CIA forged a surveillance partnership with Libya's ruler Muammar Gaddafi to spy on Libyan dissidents in the West, in exchange for permission to use Libya as a base for extraordinary renditions.
As of 2010, the Five Eyes also have access to SIPRNet, the U.S. government's classified version of the Internet.
In 2013, documents leaked by the former NSA contractor Edward Snowden revealed the existence of numerous surveillance programs jointly operated by the Five Eyes. The following list includes several notable examples reported in the media:
- PRISM – Operated by the NSA together with GCHQ and the ASD
- XKeyscore – Operated by the NSA with contributions from the ASD and the GCSB
- Tempora – Operated by GCHQ with contributions from the NSA
- MUSCULAR – Operated by GCHQ and the NSA
- STATEROOM – Operated by the ASD, CIA, CSE, GCHQ, and NSA
In March 2014, the International Court of Justice (ICJ) ordered Australia to stop spying on East Timor. This marks the first such restrictions imposed on a member of the FVEY.
In November 2020, the Five Eyes alliance criticised China's rules which disqualified elected legislators in Hong Kong.
Competition with China (since 2018)
On 1 December 2018, Meng Wanzhou, a Huawei executive, was arrested by Canadian authorities at Vancouver International Airport, in order to face charges of fraud and conspiracy in the United States. China responded by arresting two Canadian nationals. According to the South China Morning Post this conflict was seen by analysts as the beginning of a direct clash between the CCPs leadership of China and members of the Five Eyes alliance. In the months that followed, the United States placed restrictions on technology exchanges with China. Following prompting by parliamentarians in Australia and by US Secretary of State Mike Pompeo, the UK Government announced it would reduce the presence of Huawei technology in its 5G network to zero. The newspaper reported that these events were seen by Beijing as political warfare "waged with the world’s oldest intelligence alliance, the Five Eyes."
In mid-April 2021, the New Zealand Foreign Minister Nanaia Mahuta issued a statement that New Zealand would not let the Five Eyes alliance dictate its bilateral relationship with China and that New Zealand was uncomfortable with expanding the remit of the intelligence grouping. In response, the Australian Government expressed concern that Wellington was undermining collective efforts to combat what it regarded as Chinese aggression. Mahuta's remarks were echoed by New Zealand Prime Minister Jacinda Ardern who claimed that while New Zealand was still committed to the Five Eyes alliance, it would not use the network as its first point for communicating on non-security matters. While The Telegraph's defence editor Con Coughlin and British Conservative Member of Parliament Bob Seely criticised New Zealand for undermining the Five Eyes' efforts to put a united front against Beijing, the Chinese Global Times praised New Zealand for putting its own national interests over the Five Eyes.
In late April 2021, the Global Times reported that employees of companies and organisations considered to be "at-risk" of foreign infiltration travelling to the Five Eyes countries would be monitored by the Chinese Ministry of State Security. These employees will be required to report their travel destinations, agendas, and meetings with foreign personnel to Chinese authorities. Other security measures include undergoing "pre-departure spying education" and leave their electronic devices at home and bring new ones abroad. These measures came at a time of heightened tensions between China and the Five Eyes countries
-
What You Should Know About the “Five Eyes” Intelligence Community
Here’s what you should know about the partnership that has been described as the “Five Eyes,” the “world’s most exclusive intelligence sharing club”:
1. The Five Eyes (FVEY) is an intelligence community consisting of Australia, Canada, the United Kingdom, the United States, and New Zealand. The FVEY group is a cooperative, complex network of linked autonomous intelligence agencies from each of these countries.
2. The FVEY partnership began with the UKUSA agreement, first called the BRUSA Agreement. This agreement, signed in March 1946 and still in effect, was the basis for cooperation in signals intelligence between the two nations. The agreement was later extended to include former British Dominions—Canada in 1948 and Australia and New Zealand in 1956.
3. For most of FVEY’s existence, the details about the existence of the arrangement have been kept strictly confidential. The partnership was so secret that Australian prime ministers were reportedly unaware of its existence—or their country’s involvement—until 1973. The program was also not acknowledged by the U.S. or UK until 2010 when both countries declassified documents relating to the partnership.
4. The group got its name from the way intelligence products are classified. For example, a Top Secret document intended only for Canadian intel officials, explains James Cox, would be stamped as, “TOP SECRET—CANADIAN EYES ONLY.” Intelligence products to be shared with the group of closest intelligence allies are marked “SECRET— AUS/CAN/NZ/UK/US EYES ONLY.” According to Cox, in conversation allied intelligence personnel adopted the term “Five Eyes” as a form of verbal shorthand because it was easier to say than “AUS/CAN/NZ/UK/US.”
5. The FVEY partnership focuses on the subset of intelligence collection known as signals intelligence (SIGINT). SIGINT is a category of intelligence comprising all communications intelligence, electronic intelligence, and foreign instrumentation signals intelligence, however transmitted.
6. The agencies within FVEY have a uniquely open and close relationship. As one senior member of Britain’s intelligence community has said:
When you get a GCHQ [UK’s SIGINT organization] pass it gives you access to the NSA too. You can walk into the NSA and find GCHQ staff holding senior management positions, and vice versa. When the NSA has a piece of intelligence, it will very often ask GCHQ for a second opinion. There have been ups and downs over the years, of course. But in general, the NSA and GCHQ are extremely close allies. They rely on each other.
And as Richard J. Aldrich says, “Sharing in this realm [SIGINT] between the United States, the UK, Australia and Canada is so complete that national product is often indistinguishable.”
7. During the Cold War, the FVEY partners reportedly developed a global communications monitoring program known as ECHELON. The program is said to have used ground-based signal stations located around the world to collect Soviet satellite communications. Since then, the program is claimed to have developed the ability to monitor emails, fax, telephone, and Internet communications. ECHELON is believed to capture all communication traffic and sift through it for keywords or other suspicious activity.
8. The original UKSUSA agreement “evolved into a common understanding that both governments will not target each other’s citizens/persons.” However, a 2005 draft of an NSA directive says the partners “reserved the right to conduct intelligence operations against each other’s citizens “when it is in the best interests of each nation.”
9. Last year Canada announced it would temporarily stop sharing metadata with FVEY partners because the Communications Security Establishment (CSE)—Canada’s equivalent of the NSA—“did not properly minimize Canadian identity information contained in certain metadata prior to being shared.”
10. In addition to the Five Eyes alliance, a number of other surveillance partnerships exist, such as: 9 Eyes: the Five Eyes, with the addition of Denmark, France, the Netherlands, and Norway; 14 Eyes: the 9 Eyes, with the addition of Germany, Belgium, Italy, Spain, and Sweden; and 41 Eyes: all of the these countries, with the addition of the allied coalition in Afghanistan.
-
5 Eyes, 9 Eyes, & 14 Eyes Countries – What You NEED to Know
When talking about international intelligence-sharing agreements, things can get complicated fast. Don’t worry—we are going to quickly walk you through the key information about the Five Eyes, Nine Eyes, and Fourteen Eyes Alliances (9*14).
These alliances may pose a risk to your privacy, but we’ll tell you exactly what you need to do to protect your data and keep your online activity anonymous.
Find out below what these alliances are and how they can affect VPN users like you. We have also included a country-by-country guide to VPN jurisdictions.
What Is the 5-Eyes Alliance?
The Five Eyes Alliance arose out of a cold war era intelligence pact called the UKUSA Agreement. This was originally an intelligence-sharing agreement between the United States and the UK aimed at decrypting Soviet Russian intelligence.
By the late 1950s, Canada, Australia, and New Zealand had also joined the Alliance. These five English-speaking countries make up the Five Eyes Alliance as we know it today. The intelligence-sharing agreement between these five countries has only strengthened over time, as it has extended to surveillance of online activity.
For many years, this arrangement was a well-kept secret between the five nations. Its existence wasn’t discovered by the public until 2003. Things started to become clearer in 2013 after Edward Snowden leaked a number of documents that he obtained while working as an NSA contractor.
These documents exposed widespread government surveillance of citizens’ online activity and contained evidence that the international intelligence-sharing network is more extensive than previously thought.
In addition to the core nations of the Five Eyes Alliance, the existence of two other international intelligence-sharing agreements has been confirmed. These two agreements, known as the Nine Eyes and Fourteen Eyes Alliances, may not be as tight-knit as the Five Eyes Alliance, but they still have wide implications for internet privacy.
Here is a brief breakdown of each of the three Alliances:
Five Eyes: US, UK, Canada, Australia, New Zealand
Nine Eyes: Five Eyes + Denmark, France, Holland, Norway
Fourteen Eyes: Nine Eyes + Germany, Belgium, Italy, Sweden, Spain
The Nine Eyes and Fourteen Eyes Alliances are essentially extensions of the original Five Eyes Alliance. While these countries may not all share as much information with each other as the Five Eyes Alliance, they still actively and willingly participate in international intelligence-sharing.
In addition to these confirmed alliances, it is also worth mentioning another handful of countries that have been caught or suspected of exchanging information with the Fourteen Eyes Alliance.
Third Party Contributors: Israel, Japan, Singapore, South Korea.

How Can This Affect VPN Users?
The intelligence-sharing practices of these countries have wide implications for internet users and VPNs in particular. It is safe to assume that if any of these 14 nations gains access to your data online, your data can then be shared with other countries.
It all comes down to who has jurisdiction over your online activity when you are using a VPN. There are several layers to consider.
Is it your physical location? The server location? Or the VPN provider’s business location? If you really want to be safe, it is best to know the laws and practices of all three.
Knowledge is Power
You need to be aware of the online laws and regulations of the country you live in. For example, is VPN use even legal in your country? In most cases, the answer is yes, but not always.
Another important consideration is the country where your VPN provider is registered as a business. It is strongly recommended that you do not choose a VPN provider based in a country associated with the Fourteen Eyes Alliance if you are concerned about online privacy.
Depending on the country it is based in, your VPN provider could be forced to hand over information to the government about its users. This data could then be shared with other countries in the alliance. You may not even know that your privacy has been breached.
If you want to be extremely cautious, you should also be familiar with the surveillance practices of the country where the server you are using is located, regardless of the VPN provider’s business location.
Why No-Logs Policies Are Important
The many ways that VPNs can fall under the jurisdiction of various governments is why the best VPNs for privacy have strict no-logs policies. This means that they do not retain any kind of identifying information about their users or their online activity.
A great example of this policy in action comes from the well-known VPN provider ExpressVPN. A Turkish police investigation that involved an ExpressVPN user tried to compel the provider to hand over identifying data.
Despite their best attempts, authorities were unable to find any identifying information due to ExpressVPN’s strict no-logs policy.
As comforting as this story is, there are also known cases of VPN providers claiming to have a no-logs policy who then gave out users’ sensitive information to government authorities.
It may not be enough for a VPN provider to claim to offer a no-logs policy, particularly for VPN providers that fall under the jurisdiction of countries in the Five Eyes, Nine Eyes, and Fourteen Eyes Alliances.
-
Information on the Five Eyes alliance has emerged piecemeal since its birth. We now know that Five Eyes have integrated programmes, integrated staff, integrated bases, and integrated analysis.
Intelligence-sharing agreements have now expanded beyond the Five Eyes to include other states:
9 Eyes: the Five Eyes, with the addition of Denmark, France, the Netherlands and Norway;
14 Eyes: the 9 Eyes, with the addition of Germany, Belgium, Italy, Spain and Sweden;
41 Eyes: all of the above, with the addition of the allied coalition in Afghanistan;
Tier B countries with which the Five Eyes have “focused cooperation” on computer network exploitation, including Austria, Belgium, Czech Republic, Denmark, Germany, Greece, Hungry, Iceland, Italy, Japan, Luxembourg, Netherland, Norway, Poland, Portugal, South Korea, Spain, Sweden, Switzerland and Turkey;